Naked Security reader Lisa Goodlin is a website designer and a WordPress user.
That’s not exactly a secret.
If you happen to visit one of the sites she looks after, you’ll probably see her name and a link to her own website discreetly placed at the bottom of every page, as I’ve done on this site I made up to use as an example:
And why not?
It’s not just handy for Lisa as a spot of advertising, it’s handy for anyone who spots a problem with the site and wants to report it.
So that tells you she’s a web designer; finding out that she’s probably also a WordPress user (aside from the fact that it’s a good guess, being a very popular content management system for blogs and web servers) is similarly easy.
Just try adding /wp-admin to the website’s fully qualified domain name, and see if you end up redirected to a WordPress login page, something like this:

Once you get this far, you can be pretty sure that:
- info@lisagoodlin.com is a working address that will reach someone in the business of caring for websites.
- luresite.example is one of lisagoodlin.com’s customers.
- Sending emails to (1) about WordPress issues on site (2) would not be entirely out of the ordinary.
And that’s exactly what phishers did to Lisa, in what I like to call a “generic mass targeted attack.”
We’ll assume that they don’t know Lisa from a bar of soap, and that they aren’t targeting her because she’s Lisa Goodlin. (Sorry, Lisa: I don’t mean to imply you are unimportant!)
They’re targeting Lisa simply because their web crawler identified her business as a website design company that uses WordPress.
That gives them a way to phish her more believably than just hitting her up randomly, out of the blue.
What happens next
The phishers’ rogue back end server is surprisingly simple.
On a compromised web server belonging to an innocent third party, the crooks have set up some PHP scripts that simulate a wp-admin login page.
Visiting a realistic looking URL like this (don’t bother trying it: 192.0.2.0/24 is an IP range reserved for documentation only):
http://192.0.2.62/blog/wp-login.php? redirect_to=http://luresite.example/wp-admin/reauth=1
produces a realistic looking login screen like this, tailored with the text luresite.example:
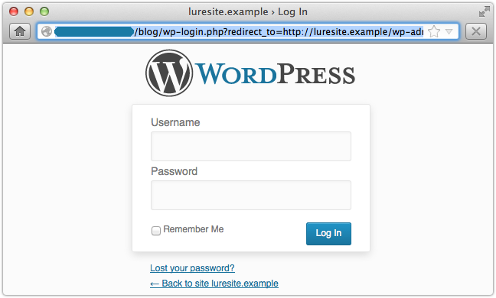
Of course, it should be obvious that something is wrong, not least because the domain luresite.example looks familiar but the starting domain, 192.0.2.62, does not.
Nevertheless, if you’re in a hurry, or just trying to tidy up a few loose ends for your customers before bedtime, you might not look carefully enough at the URL, and instead rely on two other factors:
- The presence of the text luresite.example, which lends familiarity because it’s your customer.
- The look and feel of the login screen, which is visually correct because it’s ripped off from WordPress.
If you fall for the phish, the username and password you enter are sent to the crooks, not to the luresite.example server.
Casting the bait
The next step the phishers need to take is to persuade you to click through to the login page.
And what better way of attracting a WordPress user’s attention than by means of a notification about a pending website comment?
Any switched-on web site operator who has enabled comments on a customer’s site will be putting regular and frequent effort into keeping the comments flowing: it’s a great way to attract and build an online community, and it’s fun, too.
Using comment bait is exactly what Lisa’s phishers did; fortunately, their creativity and attention to detail fell apart at this point, and she received an email like this:
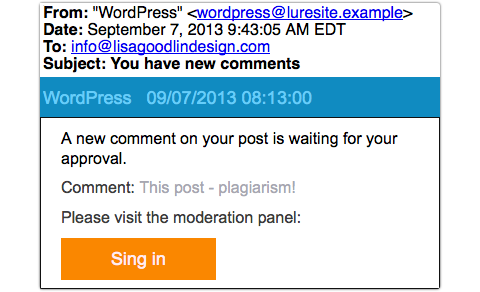
It was for amusement rather than pedagogic value that Lisa sent the phish to us – as she herself put it, “‘Sing in’! Yes, let’s all get together and sing Kumbayah!”
But it wouldn’t take much effort for the crooks to produce something significantly more believable.
What to do?
You probably frequently see emails that are obviously bogus but which nevertheless make you think, “However did they know that?”
It might be a DHL scam just after you make an online purchase from a company that uses DHL, or a promised tax refund soon after you submit your annual return, or (as in this case) an email that happens to match both your content management system and your customer.
Whenever this happens, I suggest you actually stop and take the time to answer.
Treat the rhetorical question literally and you’ll quickly realise that there are often many ways that “they could have known.”
In Lisa’s case, it was simply that her domain name was listed on a website that happens to use WordPress.
Here are some other steps you can take:
- Don’t use login links provided in emails. It’s too easy to make a mistake.
- Consider managing your customers’ websites from inside their networks via a full-blown Virtual Private Network (VPN), so you don’t need to leave the website administration portal visible to the world.
- Consider using two factor authentication for remote logins, so that your password alone isn’t enough for the crooks.
- Remember that “Sing ins” are for church choirs and choral societies, not for WordPress administrators.
More about two factor authentication
By the way, for a discussion of how two factor authentication helps protect you in cases of this sort, you might like to listen to this Techknow podcast:
(15 April 2013, duration 16’25”, size 9.9MBytes)
Article source: http://nakedsecurity.sophos.com/2013/09/08/anatomy-of-a-phish-a-generic-mass-targeted-attack-against-wordpress-admins/
