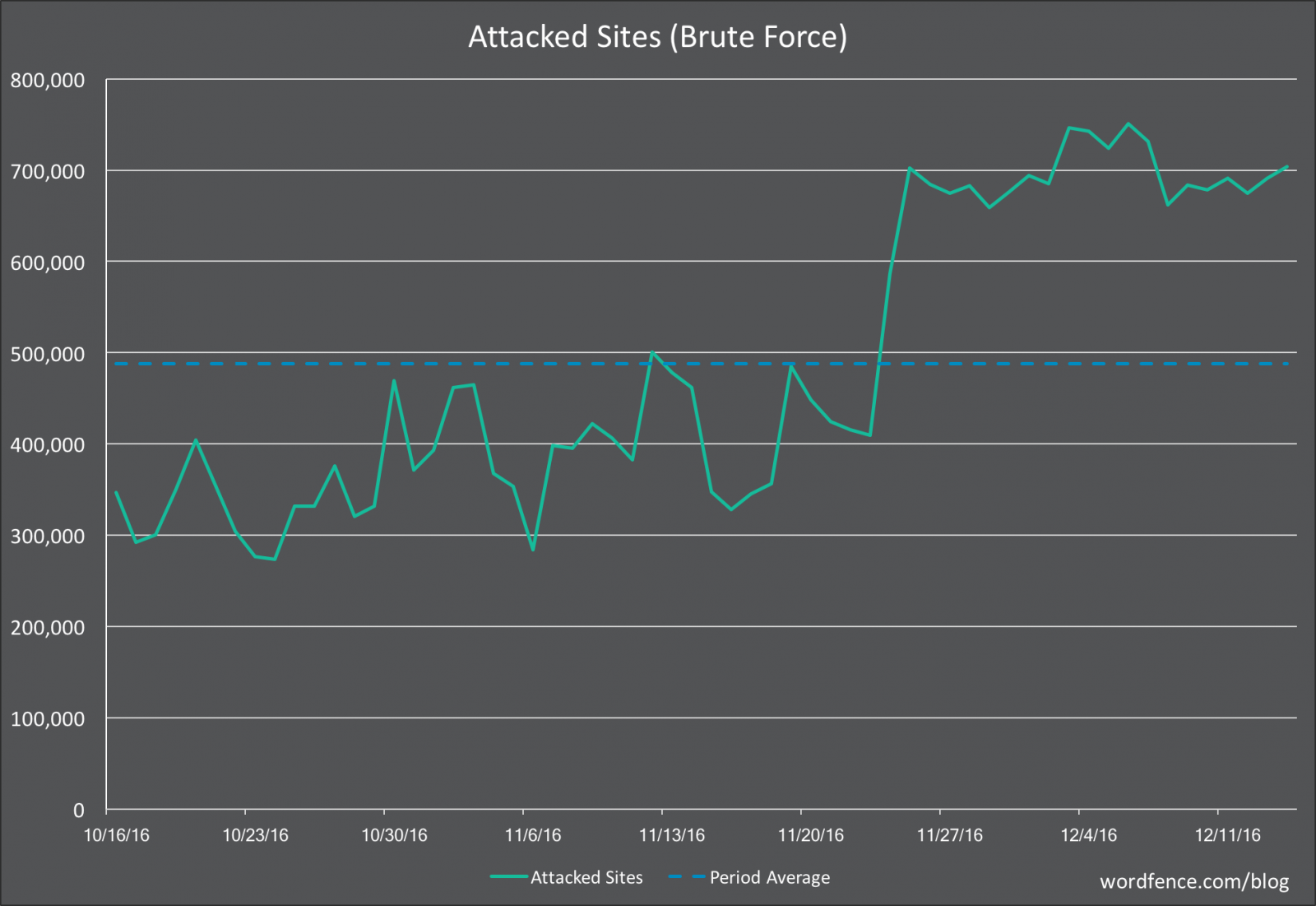
Over the past three weeks, the number of brute-force attacks against WordPress sites has almost doubled, according to WordPress security firm WordFence.
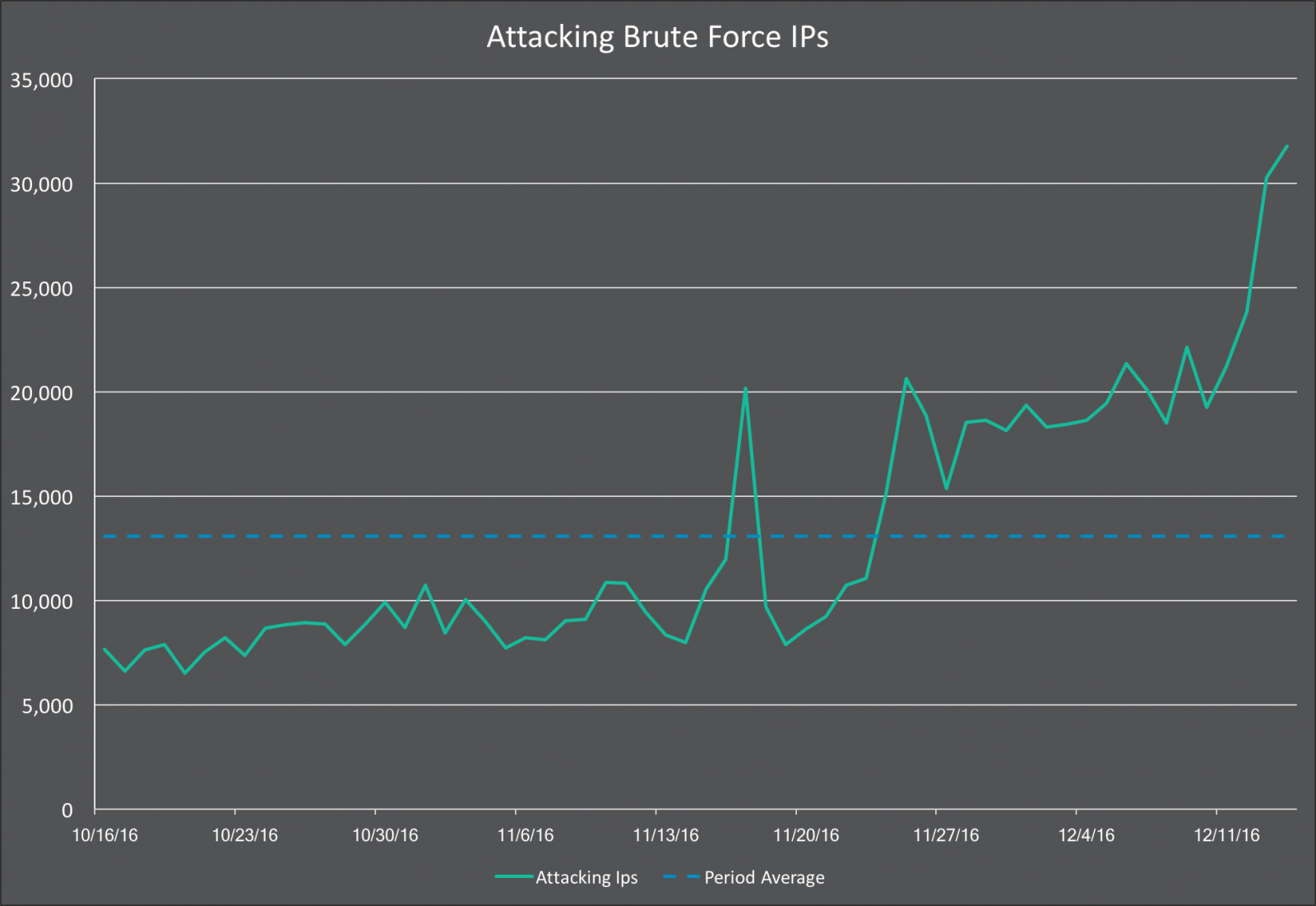
The company says it recorded a sharp increase in the number of daily attacks and daily IPs involved in brute-force requests following November 24.
Brute-force attacks are attempts to guess a websites admin (or any user’s) credentials by launching repeated authentication requests at small intervals. These attacks usually come at short time intervals, and web firewalls can detect and block them. True brute-force attacks usually involve billions of authentication attempts, as the attacker goes through all the password variations. The incidents WordFence is reporting are most likely dictionary attacks, where an attacker uses a small list of potential passwords, such as “123456” and others. Because most people, including a vast number of security firms and infosec professionals, refer to dictionary attacks as brute-force attacks, this article uses the term brute-force, albeit the correct term would be dictionary attack.
“Usually we see an average of around 13,000 unique IP’s attacking each day. We’re currently seeing over 30,000 unique attacking IPs and this is continuing to increase,” says Mark Maunder, Wordfence Founder and CEO.
Â
WordFence, who provides a free and paid version of a WordPress security plugin, was able to gather details about the source of these attacks.
One ISP behind a sixth of all brute-force attempts
The company says that most of these brute-force attempts came from one country, and more specifically, from one ISP.
According to statistics, 15.7% of all brute-force attacks on a daily basis come from the Ukraine, with over 2.3 million attacks launched each day.
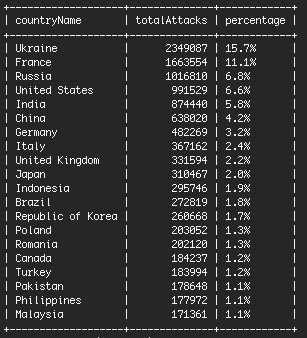
Of these, over 1.65 million came from an unknown ISP named Pp Sks-lugan, for which there’s almost no information available through Google. In fact, most of the information returned by Google is about abuse reports and security related incidents.
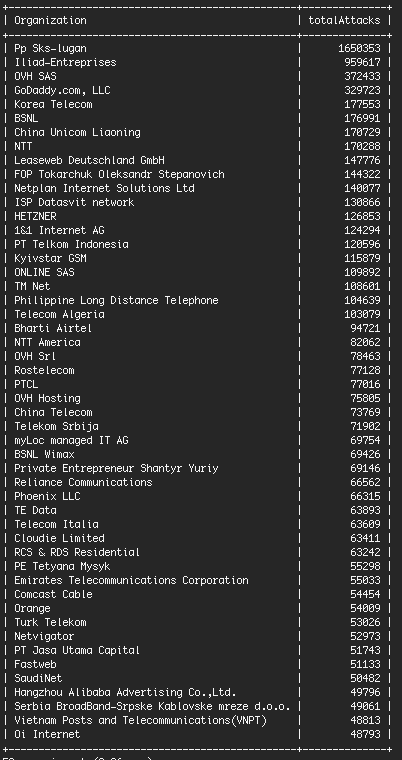
According to WordFence, over 1.5 million of the daily attacks originating from Pp Sks-lugan are launched from eight IP addresses.
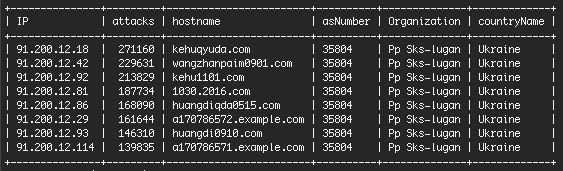
The brute-force traffic originating from these eight Pp Sks-lugan IP addresses is larger than the entire brute-force traffic coming from GoDaddy, OVH, and Rostelecom put together.
Remind you that these are some of the biggest Internet service providers and hosting companies on the planet, compared to a small Ukrainian hosting firm that nobody has heard of until now.
“The difference between the top two networks and the network in third place is dramatic,” Maunder says. “OVH is a very large hosting provider, but we’re seeing more than 4 times fewer attacks originating from their network than from the #1 Ukrainian host.”
The traffic coming out of this ISP is exclusively for brute-force attacks. “They don’t launch any sophisticated attacks,” Maunder also adds. “They are hammering away at WordPress sites at a rate of over a quarter million login attempts each, in some cases, during a 24 hour period.”
Basic protection measures
The simplest way to prevent brute-force attacks is to install a WordPress firewall plugin. If you don’t run WordPress, there are generic Web Application Firewall services or tools you can use.
If you use WordPress, another trick is to use plugins that hide your admin panel URL, so attackers can’t connect to it. Some of the plugins that allow you to do this are WP Admin Block, HC Custom WP-Admin URL, Protect Your Admin, Custom Login URL, and WPS Hide Login.
Â
Article source: https://www.bleepingcomputer.com/news/security/ukrainian-isp-behind-over-1-65mil-daily-brute-force-attacks-on-wordpress-sites/
